You know what they say: the only thing that grows faster than an organisation, is the number of vulnerabilities. I see plenty of organisations claim they know their threat vectors, and sure, you may have software and hardware designed to keep intruders out, but what about all those IoT devices and cloud services you rely on? And how about third-party apps and other assets that access sensitive data? Don’t even get started on the issues that can araise from Shadow IT! The attack surface of an organization is constantly expanding, so it’s critical to manage it with External Attack Surface Management (EASM). To help you do just that, Azure has a tool that can be used to discover, monitor and assess the external surface of your organisation with Defender for EASM. Defender for EASM will help you reduce risk by identifying potential vulnerabilities in your external environment so your security team can prioritize them based on severity or likelihood of exploitation.
The expanding attack surface
The attack surface of an organisation is the sum of all possible paths that an attacker can use to reach a system. For example, if you have a web server that runs on port 80 and you also have an internal database server that runs on port 1521, then there are two different paths an attacker can take in order to get access to your network: either directly through the web server or indirectly through the database server.
The attack surface of your organization expands over time as new systems are added to your network, but it also grows as new applications are deployed within it. If someone puts up a few web apps for internal use only (for example), these will still be part of your attack surface even though they’re not accessible from anywhere else online!
Attack Vectors
If you’re unfamiliar with the term “attack vector,” it is the way an attacker can get into a system. You may be thinking that sounds like something from a sci-fi movie, but it’s actually true! This is different from Attack surface as vectors are the methods that are exploited to gain access.
Attack vectors are constantly expanding: modern attacks often use multiple attack vectors simultaneously. The external attack surface of a system is the part of it that is exposed to the internet and thus vulnerable to attack. In other words, more things are connected to networks now than ever before (think IoT devices) and they’re all potentially vulnerable to cyberattacks as well.
The process of managing this expanding external attack surface is known as External Attack Surface Management (EASM). EASM involves identifying what parts of your systems are exposed and then taking steps to minimize those risks by reducing their exposure while still allowing them access when needed.
External Attack Surface Management and Defender for EASM.
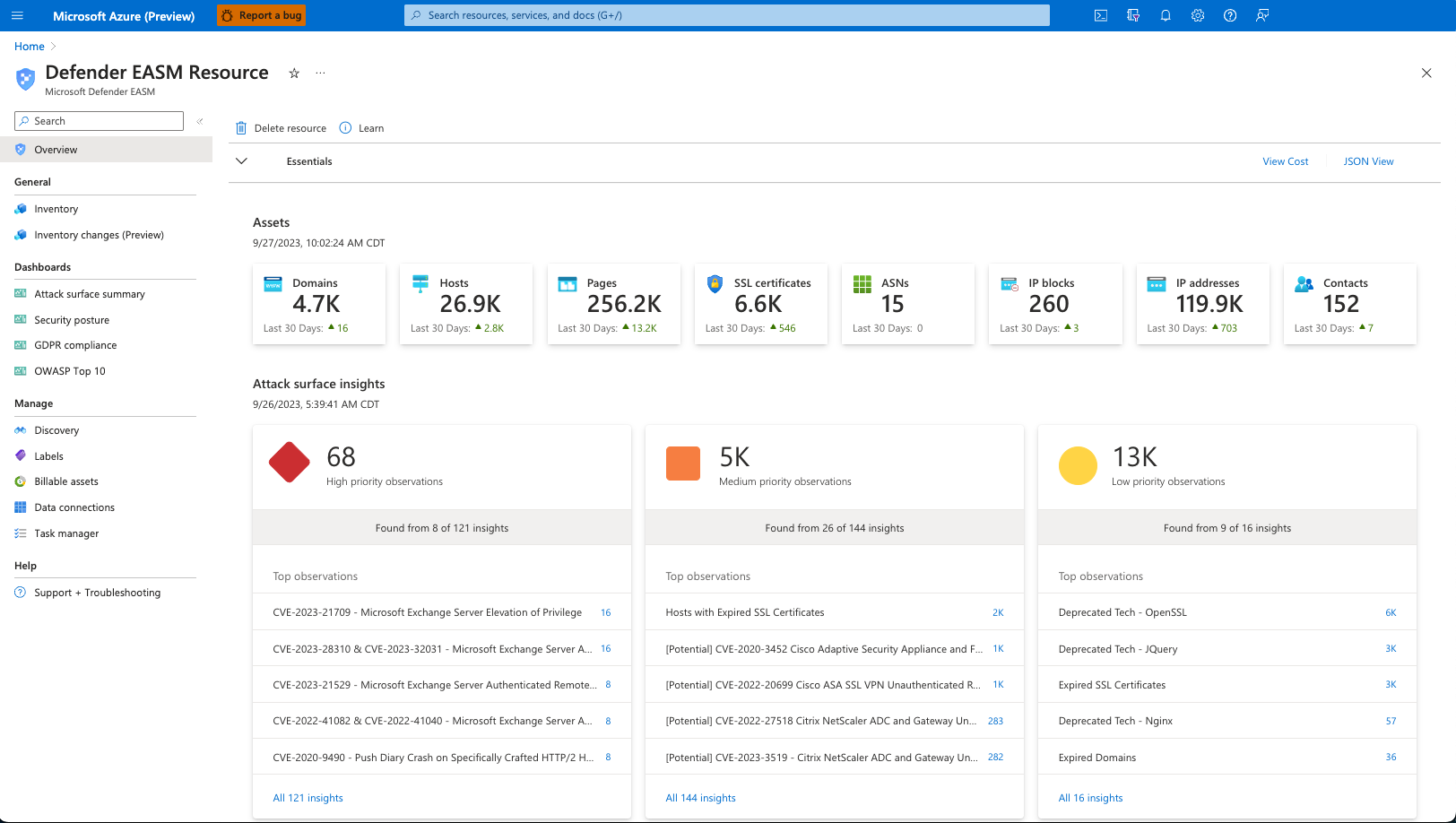
Attack surface management (ASM) is a key element in Defender for EASM (EASM), a core component of the Defender Security Platform. ASM is about understanding and reducing your external attack surface by identifying, assessing and reporting on vulnerabilities associated with all systems, services, applications and data that are exposed to the internet.
Defender EASM helps you monitor your organisation’s external attack surfaces through the use of EASM—an extensive list of thousands of predefined industry best practice checks that are constantly updated as new vulnerabilities are discovered or reported. With this information at hand, you can take action to reduce your risk profile by making informed decisions about which resources should be locked down or removed entirely from the internet—allowing you to focus on what really matters: internal security.
You can better protect your enterprise by managing your external attack surface with Defender for EASM.
Why monitor EASM? - Surely an annual audit is sufficient?
Think of your enterprise like a castle: you need to make sure that no one can get in. And while there are many things you can do and good practices you should follow to keep intruders out, it is also important to know what vulnerabilities exist and how they could be exploited by an attacker.
That’s where Defender for EASM comes in. It is a key component of the Defender for EASM solution, which helps provide a unified view of your external attack surface by identifying and managing vulnerabilities across all endpoints—virtual machines (VMs), laptops, desktops, mobile devices—that connect with the internet or any untrusted network.
Wrapping it up
The attack surface of an organization is constantly expanding. New technologies, applications and networks are being added every day, making it harder for defenders to keep up with the pace at which threats are evolving. Attackers have been one step ahead of defenders by finding new vulnerabilities and exploiting them before anyone knows about them. Defender for EASM helps you detect these vulnerabilities before attackers do in your network, so you can take action on them quickly before they cause damage or become exploited by malware or other cyber threats.
Links
Ok, I’m interested, give me those links
